BACKGROUND
A new spreading PDF has been found in the wild: “Us-J-India_strategic_dialogue.pdf" from katieedouglas@yahoo.com Thu, 7 Jan 2010 10:07:18 -0800 (PST) (thx http://contagiodump.blogspot.com/2010/01/jan-7-us-j-indiastrategicdialogue-from.html).
EXPLOITER STAGE
| FILENAME | FIND DATE | SIZE (Bytes) | MD5 | AV DETECTED |
| Us-J-India_strategic_dialogue.pdf | 7/1/2010 | 70,437 | 12AAB3743C6726452EB0A91D8190A473 |
Let's start analyzing them..
PDF doc has obfuscated directives as analyzed by extraexploit (http://extraexploit.blogspot.com/2010/01/adobe-cve-2009-4324-another-one-with.html)
This malicious PDF contains one FlatDecode (Zlib) stream that is the vulnerability exploiter; other code is, as usal, embedded in the pdf . Extracting the malicious stream reveals the JavaScript code. The code is simply hex-coded and obfuscated:
| FILENAME | EXPL STREAM OBJ | OBFUSCATION | MD5 Deflated Stream | AV DETECTED |
| Us-J-India_strategic_dialogue.pdf | #1 | FlatDecode + HexCoded | 833AA8A34B78FD3063D29314ACF3BC74 |
SHELLCODE STAGE (this.media.newPlayer )
To analyze the SC, deobfuscate/unenscape it and then it can be loaded in the debugger.
| FILENAME | SHELLCODE | EXPL STREAM OBJ | SIZE (Bytes) | MD5 Bytestream | AV DETECTED |
| Us-J-India_strategic_dialogue.pdf | 1_SC | #1 | 1,062 | D3C4FA1872F8A911565B3A1B5ABA3E5E |
AV vendors use the following names when detecting the malicious SC: Heuristic.BehavesLike.Exploit.CodeExec.EOOB
The Shellcode start function expose the self-decrypting routine (be carefull, first XOR occur at address 0x0040103E so the instruction following the JNZ are decrypted at runtime). Be sure also not have any breakpoint in code area changed at runtime, otherwise the decryption will fail xoring with INT 2 bytecode injected in code for BKP debugging:
So manually execute the first 9-10 round of the loop letting bytecode at 0x0040103E become a consistent instruction and then place a BKP there. Then RUN and decrypt all the remaining code.
As usual the SC search for address referring to external function and save them on stack; then execute its action:
1 – find the path to the malicious PDF father by GetCommandPath (it gets CommandPath and search for the 2nd occurrence of “:”, supposing that the CommandPath in Adobe exploited context will be like “C:\Program Files\Adobe\Reader x.x\Reader\AcroRd32.exe C:\bla … bla…bla\Us-J-India_strategic_dialogue.pdf”.) So to have a refer to PDF father it needs to take just the second part of CommandPath.
That’s why a simple execution of SC inside a .EXE container (as the result of SANDSPRITE SC2EXE) will fail!!.
To go on it’s possible to in-memory patch the GetCommandPath result with real path to PDF father and patch the search routine to stop on first occurence of “:” 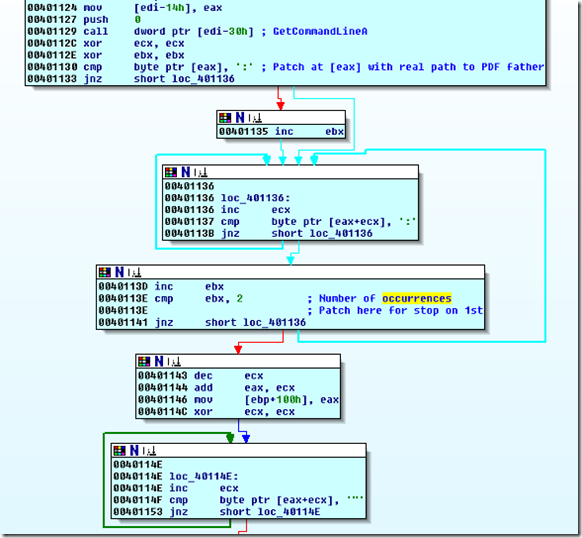
2 – then SC simply OPEN the malicious PDF father 
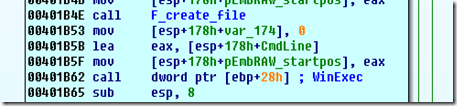
An interesting “obfuscation of function call” here: note that the CreateFileA (made also for WinExec) function call is made by JMP EAX. All the passed parameter are on the stack with the RETADDR calculated by “CALL $+5, POP EAX, ADD EAX,0DH”. Obviously the start address of function CreateFileA ([edi-4]) & WinExec ([edi-14h]) have been previously changed to work with this obfuscated calling method, adding 5 byte to the function starting address: 

3 – back to the SC, it create a temp file in temp path 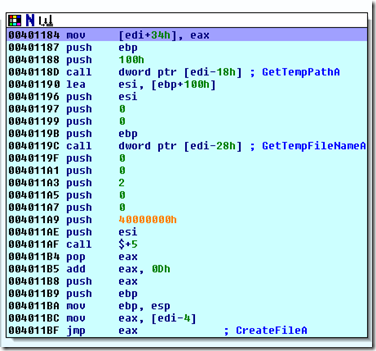
4 – set file pointer to 1000H from SOF 
5 – read #7 blocks of 400h bytes each from PDF father, decrypt each block in memory and append it to the temp file.
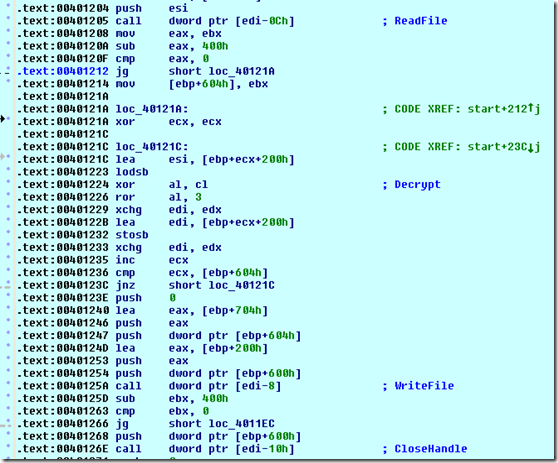
6 – last step WinExec the tem file extracted from PDF father

The level 1 malware has been dropped and executed!!
LEVEL 1 MALWARE STAGE (this.media.newPlayer )
| FILENAME | SHELLCODE | EXPL STREAM OBJ | SIZE (Bytes) | MD5 Bytestream | AV DETECTED |
| random.tmp | 1_SC | #1 | 7,168 | 37AB49086946056449F0ED1ACF80470C |
A first look reveal unusefull instruction & invalid bytecode just placed there to get debugger disasm display in trouble.

JZ and JNZ simply let code flow go on, jumping over the invalid bytecode E7h. That’s method is repeated several times (#120) in the code.
So to analyze random.tmp, that’s a PE file, in section “.text” (raw addr 400h, raw size 1200h) patch any hex-string “OF 84 07 00 00 00 0F 85 01 00 00 00 xx” with NOP (13x 90h), keeping section size unchanged and code relative jmp offset.

Let’s see what Level 1 malware do:
1– get its full path and set a registry startup key HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\BITS to be executed at each reboot (strings like key and value are decrypted at runtime..)
2- try for 3 times with a delay of 10 min to InternetOpenUrl: http://nyralang.zyns.com/album/index.htm
with UserAgent ‘Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)’ using Internet system configuration (INTERNET_OPEN_TYPE_PRECONFIG) and with INTERNET_FLAG_RELOAD to retrieve the original item, not the eventually cached one by a proxy.

The domain is now 14/1/2010 deactivated
but at 2010-01-07 was associated to IP 202.153.103.82 (AS9925) that still now is hosting the webpage and now is referenced by for.toh.info.
% [whois.apnic.net node-1]
% Whois data copyright terms http://www.apnic.net/db/dbcopyright.html
inetnum: 202.153.96.0 - 202.153.127.255
netname: POWERBASE-HK
descr: 6/F, Somerset House
descr: TaiKoo Place, Quarry Bay,
descr: Hong Kong
country: HK
admin-c: PD28-AP
tech-c: PD28-AP
mnt-by: APNIC-HM
mnt-lower: MAINT-HK-HKTDCS
changed: hostmaster@apnic.net 20000419
changed: hostmaster@apnic.net 20001023
changed: hostmaster@apnic.net 20020219
status: ALLOCATED PORTABLE
source: APNIC
role: Powerbase Datacenter NOC
address: 6/F, Somerset House
address: TaiKoo Place, Quarry Bay,
address: Hong Kong
country: HK
phone: +852-2312-9111
fax-no: +852-2504-0599
e-mail: support@pbase.net
admin-c: PD50-AP
tech-c: PD50-AP
nic-hdl: PD28-AP
mnt-by: MAINT-HK-HKTDCS
changed: nw_admin@pbase.net 20070306
source: APNIC
Webpage seems a normal under construction 
except for it’s first line in HTML code: a comment
<!—DOCHTMLTuichu –> 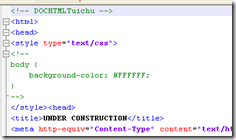
3- malware read the first 0x1FFh bytes of webpage in a buffer 
4- parse command for value “Tuichu”, “Xiuma” e “http://” 
Tuichu –> DO NOTHING, wait 10 min then retry.
Xiuma –> DO NOTHING, don’t wait and retry.
http:// –> DOWNLOAD AND EXECUTE, wait 10 min then retry
The downloaded file must have an extension but not .exe. Infact it is copied in temp path and malware create a copy of file with .exe extension and execute it.
As told before now the command deployed by C&C is “Tuichu” so the BOT are waiting…