BACKGROUND
Recently CVE-2009-4324 is related to a vulnerability in the Doc.media.newPlayer method in Adobe Reader and Acrobat 8.0 through 9.2, and possibly earlier versions. The flaw allows remote attackers to execute arbitrary code and is exploited in the wild in December 2009.
Adobe has published an updated Security Advisory. They plan to make an update available on January 12th.
Also noteworthy, this PDF vulnerability has been added to Metasploit.
EXPLOITER STAGE
Nowadays 5 malicious PDF have been discovered in the wild, all collected by received mail (tks to Contagiodump):
| FILENAME | FIND DATE | SIZE (Bytes) | MD5 |
| note200911.pdf | 30/11/2009 | 400,918 | 61baabd6fc12e01ff73ceacc07c84f9a |
| note_20091210.pdf | 11/12/2009 | 400,918 | 61baabd6fc12e01ff73ceacc07c84f9a |
| Outline of Interview.pdf | 13/12/2009 | 400,918 | 35e8eeee2b94cbe87e3d3f843ec857f6 |
| merry christmas.pdf | 18/12/2009 | 1,226,811 | 8950bbedf4a7f1d518e859f9800f9347 |
| 「寶貝悶」瘋狂照.pdf | 18/12/2009 | 51,822 | 955bade419a9ba9e5650ccb3dda88844 |
AV vendors use the following names when detecting the malicious PDF document: Exploit.JS.Pdfka.atq (Kaspersky) - Exploit:W32/AdobeReader.UZ (F-Secure) - Exploit-PDF.ag (McAfee) - Trojan.Pidief.H (Symantec) - TROJ_PIDIEF.PGS (Trend Micro)
Let's start analyzing them..
All malicious PDF contain a FlatDecode (Zlib) stream which is the vulnerability exploiter. Extracting the malicious stream reveals the JavaScript obfuscated code. The code is simply byte-by-byte xored (so it's simple to change it to be FUD) and/or escaped:
| FILENAME | EXPL STREAM | OBFUSCATION | MD5 Deflated Stream |
| note200911.pdf | #2 | XORED + ESCAPED | A48DE372FC64BCABCE5BAD6FF98F8BC0 |
| note_20091210.pdf | #2 | “ | A48DE372FC64BCABCE5BAD6FF98F8BC0 |
| Outline of Interview.pdf | #2 | “ | A48DE372FC64BCABCE5BAD6FF98F8BC0 |
| merry christmas.pdf | #156 | 4F9B900ABA7781335F99D49A896B4586 | |
| 「寶貝悶」瘋狂照.pdf | #3 | HEXED + ESCAPED | 0E63A465066B0C0A6AAA56C1925DE3FC |
So we have 3 different exploiter. One common to the first 3 PDF, and other two related to the latest malicious PDF.
SHELLCODE STAGE
To analyze the SC, unxored/unenscape it and keep in mind of byte swap due to different format in memory and stored on disk, or directly use Shell2Exe (tks to Sandsprite). Then shellcode.exe can be loaded in the debugger.
| FILENAME | SHELLCODE | EXPL STREAM | SIZE (Bytes) | MD5 Bytestream |
| note200911.pdf note_20091210.pdf Outline of Interview.pdf | | #2 | 3,094 | D0C1C15E8C37936E9E199F1F8BAD5A8F |
| merry christmas.pdf | MERRY_SC | #156 | 460 | F6EA8AA206BDE8BE2B339FE4478C271B |
| 「寶貝悶」瘋狂照.pdf | OTHER_SC | #3 | 594 | 51F1AA0CB6B3E9EF373E3E887D427DD4 |
>> NOTE_SC
The start function is:
The F_main revealed that:
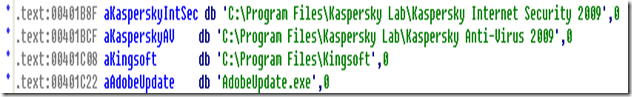
1- shellcode check for presence of software "Kaspersky Internet Scanner", "Kaspersky AV" or "Kingsoft". If detected shellcode will exit without damage. WHY?? Make your own choice or add a new one:
- The PDF was done for a specific targetted attack
- Malguys don't want to be tracked by Kaspersky/Kingsoft
- Malguys don't want to infect themselves!!!
!This check can be used as countermeasure against infection by creating false installation directory of such program! (sc check for the first file or directory found in the following directory):
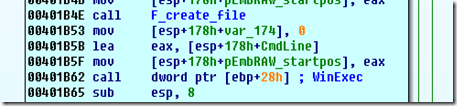
2- shellcode find handle of PDF file it was executed from scanning all existing handle for a file, greater than 6A2H bytes in size and with a specific signature 98H 76H 54H 32H at offset –1698d (-6A2H) from EOF. If not found shellcode will exit without further action.
3- shellcode then extract from PDF an embedded raw file finding the start offset with a specific signature “1C 0A D1 20 D1 CE F0 27 10 F8 2F EC AC”
followed by embedded file size (in this case 0002A000h bytes)
4- then the embedded file is dumped on disk in file setup.exe, and is executed
That's the level 1 dropper!!
Update soon about….
>> MERRY_SC
>> OTHER_SC
LEVEL 1 DROPPER STAGE







Great analysis, keep up the good work. I am attempting to analyse this for my blog. However, I want to step through this in the context of a debugger and cannot get the exploit to launch. Adobe terminates... Any ideas as to why this is?
ReplyDelete