Slowly the truth is cooming out…
The IE 0day vulnerability has been used in two scenario till now.
In first time for a targetted & silent attack against many worldwide companies finalized to intellectual properties stealing in operation “Aurora” through set up of Trojan.Hydraq bots (http://www.symantec.com/connect/blogs/trojanhydraq-incident).
Nowadays after the vuln became public, it’s going to be widely used for common malware spreading to the Mass (http://extraexploit.blogspot.com/2010/01/cve-2010-0249-in-wild-xx2228866org-and.html).
A quickly compare show that:
- IE exploitation was in both case based on heavily-encrypted javascript exploit. Aurora’s “yellow” boys probably targetted employers and public known mail accounts with fake&but trustable social engineered e-mail, convincing them to go on first malicious hosting site. Instead “scrounger” malguys are now injecting malicious iframe in “high contact volume” forum and website.
- Shellcode used was similar: Yellows code COMELE cause a connection to demo1.ftpaccess.cc/demo/ad.jpg downloading a malicious, XOR-encrypted binary that is detect as Trojan.Hydraq/Roarur.dr. 
This file is saved to %Application Data%\a.exe, such as "C:\Documents and Settings\User\Application Data\a.exe". A.exe is decrypted to b.exe in the same directory and executed. 
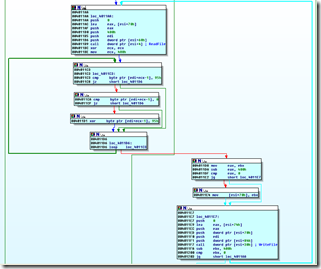
It seems that Scroungers just take SC from Comele used in “Aurora” and modified it, changing 2nd stage download URL and removing its decrypting code.
Code from Comele
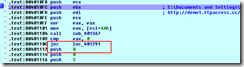
Modified actual code (an absolute JMP overwrite a conditional jnz and bypass piece of code – 2nd stage decrypt - unusefull to Scroungers)

So modified code simply donwload a malicious binary, saving it as "C:\Documents and Settings\User\Application Data\f.exe” and execute it. 
- 2nd stage malware is obviously quite different: Trojan.Hydraq / Roarur in first case; two version (down.css and log.css) of a generic malware in the second.
Virustotal Trend
| Filename | 2010.01.19 (UTC) | 2010.01.20 (UTC) | 2010.01.21 (UTC) |
| down.css | |||
| log.css |
SUMMARY
| Threat | IE exploit | Shellcode | 2nd stage malware | 3rd stage malware |
| Operation Aurora | supposed social engineered targetted email | |||
| IE CVE-2010-0249 Exploiting the mass… | injected iframe in forum/website | Modified Comele | Generic Trojan | na |

No comments:
Post a Comment